Enhancing Cyber Security: Exploring Zero Trust
In today’s digital age, the importance of robust cyber security measures cannot be overstated. As organizations increasingly rely on technology to conduct their operations, the risk of cyber threats and data breaches looms larger than ever before. To combat these evolving challenges, organizations are turning to innovative approaches, with one of the most promising being Zero Trust. In this blog post, we’ll delve into what Zero Trust is, its benefits, and how organizations can leverage it to bolster their cyber security defenses.
Understanding Zero Trust
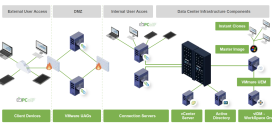
Zero Trust is not just a concept; it’s a comprehensive security framework designed to minimize the risk of data breaches and unauthorized access by assuming that threats exist both inside and outside the organization. Unlike traditional security models that rely on a perimeter-based approach, where trust is given to users or devices within the corporate network, Zero Trust adopts a “never trust, always verify” mindset.
At its core, Zero Trust operates on the principle of continuous verification and strict access controls. It involves verifying the identity of users and devices before granting access to resources, regardless of whether they are inside or outside the corporate network. This means that trust is never assumed, and every access request is scrutinized, authenticated, and authorized based on contextual factors.
Benefits of Zero Trust in Cyber Security
1. Enhanced Data Protection: Zero Trust ensures that data is protected at all times. By continuously verifying the identity and security posture of users and devices, sensitive information is safeguarded from unauthorized access.
2. Reduced Attack Surface: Traditional perimeter-based security leaves organizations vulnerable to attacks once the perimeter is breached. With Zero Trust, the attack surface is greatly reduced, as access is granted on a need-to-know and need-to-use basis.
3. Improved Insider Threat Detection: Zero Trust allows organizations to monitor and detect suspicious behavior, even from trusted insiders. This proactive approach helps identify and mitigate insider threats before they escalate.
4. Adaptability to Modern Work Environments: With the rise of remote and mobile work, the traditional corporate network boundary has become porous. Zero Trust adapts seamlessly to these modern work arrangements by ensuring that users and devices are authenticated and authorized, regardless of their location.
5. Compliance and Regulatory Alignment: Many industries have stringent data protection regulations. Implementing Zero Trust can help organizations align with these regulations and demonstrate their commitment to data security.
Implementing Zero Trust in Your Organization
Adopting a Zero Trust framework involves a strategic and phased approach. Here are the key steps to get started:
1. Assessment: Begin by assessing your organization’s current security posture and identifying vulnerabilities and weak points.
2. Define Access Policies: Develop comprehensive access policies based on the principle of least privilege. Ensure that users and devices are authenticated and authorized according to these policies.
3. Identity and Access Management (IAM): Invest in robust IAM solutions to facilitate secure user authentication and access control.
4. Network Segmentation: Implement network segmentation to compartmentalize resources and limit lateral movement within the network.
5. Continuous Monitoring: Employ advanced monitoring and analytics tools to continuously monitor user and device behavior for anomalies and potential threats.
6. User Education: Train your employees on the principles of Zero Trust and the importance of safe online practices.
7. Regular Audits and Updates: Periodically audit and update your Zero Trust policies and technologies to stay ahead of evolving threats.
As cyber threats continue to evolve and become more sophisticated, organizations must adopt modern security frameworks like Zero Trust to safeguard their data and operations effectively. The benefits of Zero Trust, including enhanced data protection, reduced attack surface, and adaptability to modern work environments, make it a valuable addition to any organization’s cyber security strategy. By implementing Zero Trust, organizations can better protect themselves in an increasingly digital and interconnected world, ensuring the safety and security of their valuable assets.
In the realm of cyber security, adopting a Zero Trust framework is not just a choice; it’s a necessity to stay one step ahead of cyber adversaries. Contact us today to learn how AMS Networks can assist implementing Zero Trust architecture.