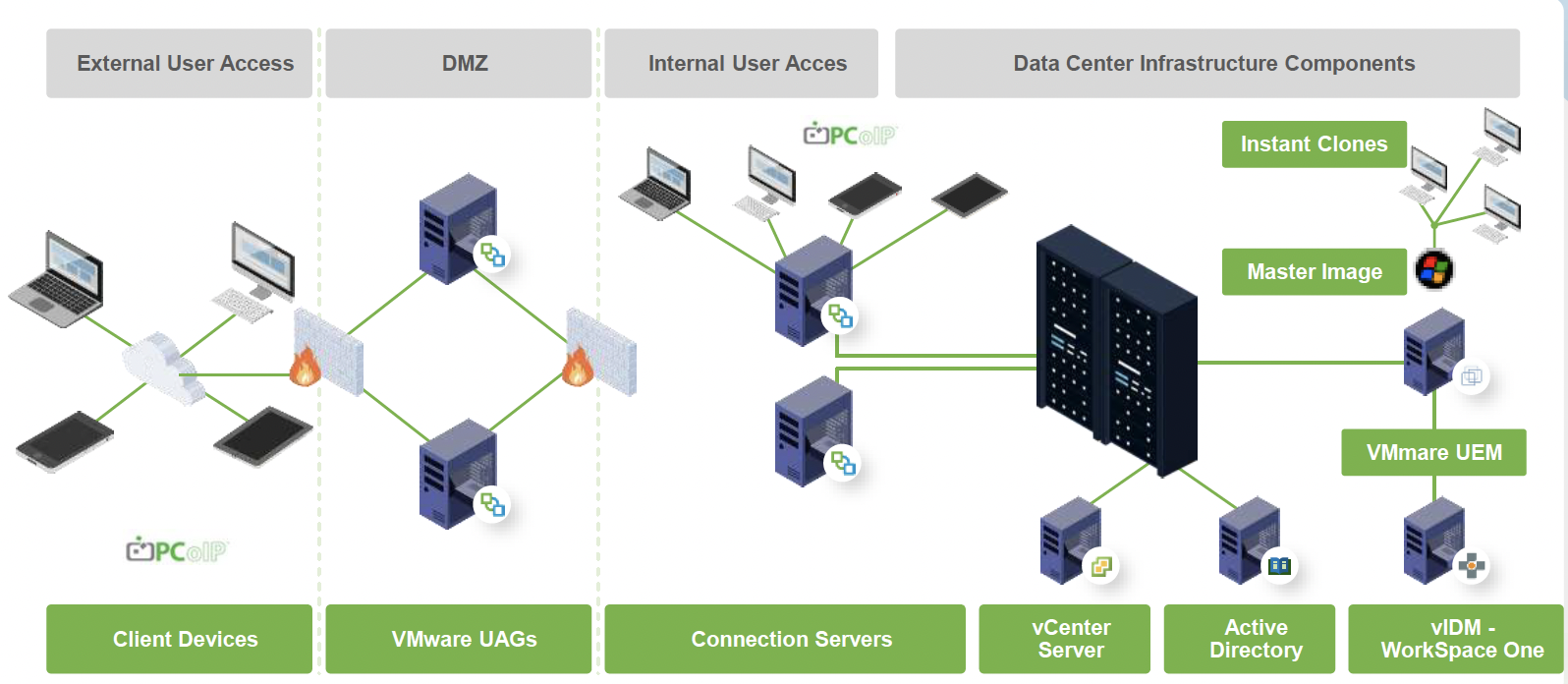
Empowering Remote Work: The Advantages of Horizon VDI for Securing Corporate Data
In the wake of the digital revolution and the global shift towards remote work, businesses face new challenges and opportunities. As the traditional office model evolves, organizations must adapt to ensure that their data remains secure while their employees work from home or remote locations. One powerful solution that has emerged to address these challenges […]
Read More »