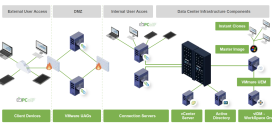
Strengthening the Cybersecurity of Federal Agencies by enhancing the HVA Program
In late 2018, White house put forward a memorandum, M-19-03 that served as a guidance urging Federal agencies to enrich their cybersecurity posture through enhancing the High Value Asset (HVA) program: White House Memorandum. This memo listed several expectations in the following areas:
- Establishing Enterprise HVA Governance
- Improving of Designation of HVA
- Implementing Data-Driven HVA Prioritization
- Increasing the Trustworthiness of HVAs
- Protecting Privacy and HVAS; and
- Defining HVA Reporting, Assessment and Remediation Requirement.
So how can agencies enhance their cybersecurity capabilities given this memorandum? Let’s look at each one of them:
- Establishing Enterprise HVA Governance
Agencies must adopt a high-level approach and setup internal team or office to structure and enable incorporation of HVA activities: assessment, remediation, incident response into broader activities of Enterprise Risk Management, Capital Planning and Investment Control (CPIC), Contract Management and Contingency Planning.
- Improving of Designation of HVA
Agencies must adopt a wholistic approach to identify and designate HVA and critical assets which can be based on potential impact of National Security.
- Implementing Data-Driven Prioritization
Agencies must allocate resources that has the ability to continuously prioritize HVA assets for better visibility and support.
- Increasing Trustworthiness of HVAs
It is a requirement to have substantial investment into the architecture, design and development of systems that enhance cyber security posture following the NIST SP 800-160 guidelines. This includes security, privacy and design requirements for HVA assets.
- Protecting Privacy and HVAs
It is a federal mandate to protect and establish requirements to property create, collect, process, store, maintain, disseminate, disclose or dispose of Personal Identifiable Information (PII). Agencies must have a formal plan and privacy controls in order to meet the objectives of protecting PII as well as HVA assets.
- Defining Reporting, Assessment and Remediation Requirements
Agencies must report all of their designated HVAs to DHS. Agencies must also have periodic testing and evaluation of the effectiveness of information security and privacy controls to ensure it has a healthy cybersecurity posture in relation to the HVAs. There must also be a formal remediation plan to address HVA findings which is continuous and ever evolving to ensure the changing landscape of cybersecurity threats.
So how can AMS Networks help? Our resources are experienced with supporting Nations most vital applications to include Customs and Border Protection’s Global Entry, Automated Passport Control, Trusted Traveler programs. We have been successful at protecting PII data through continuously monitoring and assessments. Our personnel have been part of DoD’s Cyber Security Readiness Inspection where we have supported classified and unclassified systems deemed as HVAs and created policies and procedures to standardize, protect and harden assets based on outstanding vulnerabilities.
Contact us today and learn how we can ensure that your agency has a solid cybersecurity HVA Asset program.